Louisiana School District Notifies Data Breach Victims After News Investigation
After reporters revealed thousands had their sensitive info leaked online, AG’s office issued notification warning to St. Landry schools, emails show.
Get stories like this delivered straight to your inbox. Sign up for The 74 Newsletter
This story was produced in partnership with The Acadiana Advocate, a Louisiana-based newsroom.
Individuals whose sensitive information was made public after a July 2023 cyberattack on the St. Landry Parish School Board were not notified for five months — long after state law mandates and only after a newspaper investigation prompted the Louisiana Attorney General’s Office to contact the district and warn school officials of their obligations.
The long-delayed notification was revealed in emails and other records obtained by The Acadiana Advocate this month in response to a Jan. 9 public records request.
They showed that within hours of the reporters revealing that a data breach exposed sensitive information about thousands of teachers and students, a lawyer with the state attorney general’s office was on the phone to the school district. The attorney, focused on consumer protection, questioned them “directly in response to the article,” one email states.
The Dec. 4 investigation, co-published by The Advocate and The 74, contradicted school district assertions that no sensitive student, employee or business owners’ information had been exposed online after the July attack. It found the St. Landry Parish School Board likely violated a state data breach notification law when it failed to notify victims or the state attorney general for months.
L. Christopher Styron, the lawyer with the state attorney general’s office, reacted swiftly, calling the district to inquire about the incident. He followed up with an email outlining St. Landry’s data breach response obligations under state law — rules that school officials had failed to follow.
Under Louisiana’s breach notification law, schools and other entities are required to notify affected individuals “without unreasonable delay,” and no later than 60 days after a breach is discovered. Entities that fail to alert the state attorney general’s office within 10 days of notifying affected individuals can face fines up to $5,000 for each day past the 60-day mark.
The late-in-the-year series of events prompted St. Landry officials, who long held that no sensitive data was stolen or published online, to take action. Officials told state lawyers it alerted victims that their information had been compromised. It’s unclear how many victims among thousands of students, district employees and local and out-of-state businesses, received the letter. Medusa, a nefarious cybercrime syndicate that has carried out numerous devastating attacks on school districts in the last year, took credit for the St. Landry breach.
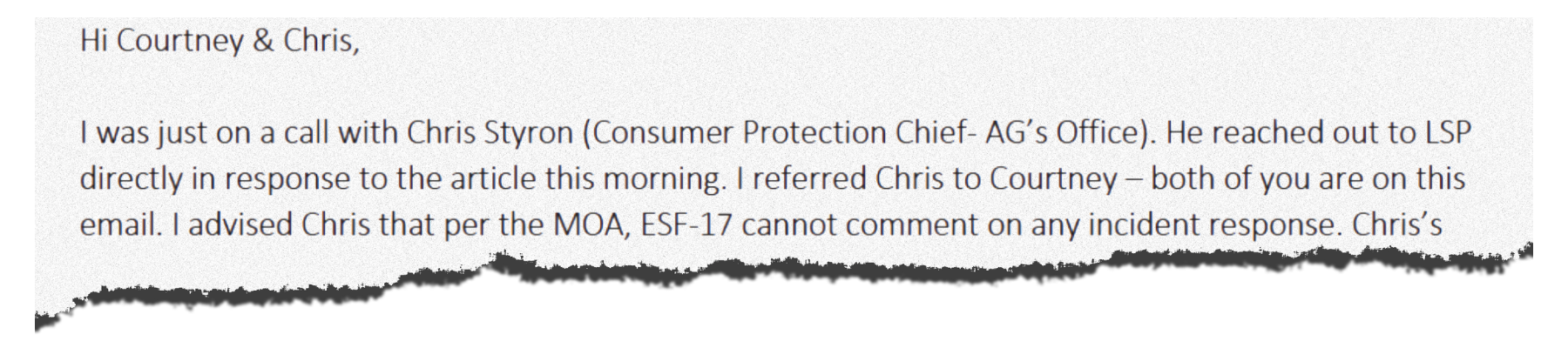
The school board’s attorney Courtney Joiner wrote in a response email to Styron a day later that he was “working with the School Board to address the notice issue without further delay.”
In a letter dated Dec. 21, schools Superintendent Milton Batiste III acknowledged to an unverified number of victims that “sensitive information may have been obtained by an unknown malicious third-party,” according to the records. Officials didn’t send a formal notice to the attorney general’s office until Jan. 10, a day after The Advocate filed its public records request.
Donna Sarver, who worked as a math teacher in St. Landry for three years before leaving in 2020, is among those whose personal information was compromised. In an interview last week, she blasted the district for sending her a letter in the mail “well after the fact” that she had been victimized.
“I really thought it was too little, too late,” she said. “This should have happened much earlier.”
Sarver and other data breach victims, including parents, students and business owners whose tax records are held by St. Landry schools, were unaware until the late December notification that district leaders had failed to secure their sensitive information and left them unknowingly exposed to identity theft for months.
It took the district 149 days after the breach to tell victims they “may have been impacted by the incident” and another 19 to formally notify the attorney general.

Officials with the school board declined to answer any questions for this story. A list of written questions were submitted but officials had yet to respond by the time of publication. The attorney general’s office didn’t respond to interview requests.
St. Landry’s response resembles that of school districts across the country, investigative reporting by The 74 has revealed. Cybergangs have ramped up their attacks on school districts and now routinely threaten to leak sensitive files in a bid to coerce seven-figure ransom payments. As federal officials warn of the burgeoning threat’s impact on students and teachers, education leaders nationwide have sought to downplay the attacks’ severity and obscure any subsequent harm to individuals.
James Lee, the chief operating officer of California-based Identity Theft Resource Center said the delay by St. Landry officials is “reflective of a problem we have” nationally where cyberattack victims have grown increasingly resistant to filing breach notices.
“In many instances, it’s because the decision to issue a notice resides 100% with the organization that loses control of the information,” Lee said. “Highlighting circumstances like this will help us address these gaps so we can get better notifications to consumers when their information has been compromised and they’re at risk.”
‘For reasons that are unknown’
In August 2023, the 12,000-student district some 63 miles west of Baton Rouge acknowledged its computer network had come under attack but told the public the breached servers didn’t contain any sensitive employee or student information.
But The 74’s data analysis of some 211,000 leaked records revealed they contained the Social Security numbers of at least 13,500 people, some 100,000 sales tax records for local and out-of-state companies and several thousand student records including home addresses and special education status.
Similarly, the district appeared to offer inaccurate, misleading and contradictory claims in its delayed response to the attorney general, its letter to data breach victims and statements to the press.
In its letter to the AG’s office, the district stated that the stolen files had been “recovered.” However, a check by The 74 last week revealed they remain readily available for download on Telegram, the encrypted social media platform Medusa uses to make public the records of victims who don’t pay to keep them private.
Superintendent Batiste wrote in that Jan. 10 notice that the district’s computer network had been encrypted by “a malicious person or group” in July but that St. Landry had never received a ransom demand.
Yet, among the cache of district documents available on Telegram is a text file titled “LOOK!!!!,” which includes a link to Medusa’s dark-web outpost, complete with a $1 million ransom demand and a countdown clock warning education leaders their time to respond is running out. The note also contained links to Medusa’s Telegram channel and to a website designed to resemble a technology news blog — a front of sorts — with a video highlighting the St. Landry records in its possession.
It was in August 2023, that the Louisiana State Police Cyber Crime Unit notified school officials that “an unknown number of files containing sensitive information” had been compromised, the letter states. That same month, Batiste had assured the public otherwise.
Files posted to a Medusa leak site “were recovered by the Cyber Crime Unit” with the state police, Batiste’s letter continues, “but, for reasons that are unknown, the files recovered from the dedicated leak site by the Cyber Crime Unit were not provided to us until December 6” — two days after the newspaper investigation published.
‘How do you recover it?’
The cybercriminals behind the St. Landry breach employed “double extortion,” a growing ransomware strategy where hackers break into a victim’s computer network through phishing emails, download compromising records and lock them with an encryption key. Criminals demand a ransom payment from victims to unlock the encrypted files and leak them online if they refuse to pay. The stolen information is routinely flaunted on the dark web and other shady corners of the internet.
In asserting to reporters last year that the Medusa hack didn’t lead to a breach of sensitive information — despite overwhelming evidence that it had — district officials acknowledged they hadn’t taken any steps to understand the scope of what was stolen or to notify individual victims.
Byron Wimberly, the district’s computer center supervisor, insisted at the time that sensitive records had not been stored on the hacked servers. The files that were uploaded by the ransomware gang, he suggested, must have originated somewhere other than St. Landry schools — even though thousands of them contain district letterhead and more than a dozen victims verified the validity of their stolen information.
Tricia Fontenot, the district’s supervisor of instructional technology, told reporters late last year that law enforcement investigators had never filled them in on the stolen data or if any sensitive information had been leaked at all.
“We never received reports of the actual information that was obtained,” Fontenot said. “All of that is under investigation. We have not received anything in regard to that investigation.”
Fontenot’s statement contradicts Batiste’s timeline to the AG saying state police informed them in August that files containing sensitive information had been accessed. A state police spokesperson said in an email last week the agency finished its investigation on Aug. 20.
Reached by phone last week, Fontenot declined to comment.
The Dec. 21 letter that school officials sent to data breach victims states that the district was hacked by “an unknown malicious” threat actor but isn’t explicit to recipients about whether their information was included.
It remains unclear how many of the thousands of data breach victims identified in the news outlets’ investigation — including teachers, staff, students and sales tax filers from across the country — received the Dec. 21 notice.
The data breach letter states that victims were being notified months after the incident because “the process of obtaining and then reviewing the acquired files took several months.”
“We are now in the process of notifying individuals whose personal information we believe to have been included in the acquired files, including you,” the letter states, acknowledging that stolen information contains individuals’ names, addresses, birth dates, Social Security numbers and driver’s licenses.

Louisiana’s data breach notification law doesn’t apply to some types of sensitive files exposed in the breach, such as student disciplinary records.
School districts nationwide, along with other government agencies and for-profit companies, routinely hire cybersecurity experts and attorneys to investigate the scope of data leaks and to notify breach victims in compliance with state laws, partly because of the complexities involved. A federal breach notification law doesn’t exist and state requirements vary.
School officials told reporters last year they expected law enforcement to investigate the attack’s impact on individual data breach victims. Lee of the nonprofit Identity Theft Resource Center said such a practice would be highly unusual.
Sign-up for the School (in)Security newsletter.
Get the most critical news and information about students' rights, safety and well-being delivered straight to your inbox.
“In fact, I don’t think I’ve ever heard of that kind of arrangement,” he said. “Most organizations do hire their own cybersecurity experts whether it’s a school district or it’s a nonprofit or a commercial entity.”
Sarver, the former St. Landry math teacher, said school leaders left data breach victims to fend for themselves by waiting months to tell them their personal information had come up for grabs on a website maintained by criminals.
While the district offered a year of credit monitoring — a common practice after entities suffer data breaches — Sarver said she decided not to enroll. The service would last just 12 months; her records could be available forever.
“How do you recover it once it’s out there?” she said. “Do you tell the people who got it illegally that you have to take it down and hope they do?”
This story was supported by a grant from the Fund for Investigative Journalism
Get stories like these delivered straight to your inbox. Sign up for The 74 Newsletter

;)
