Hackers Use Stolen Student Data Against Minneapolis Schools in Brazen New Threat
Video posted online — and then removed — by ransomware gang claimed to highlight stolen files as criminals demand $1M after ‘encryption event’
Get stories like this delivered straight to your inbox. Sign up for The 74 Newsletter
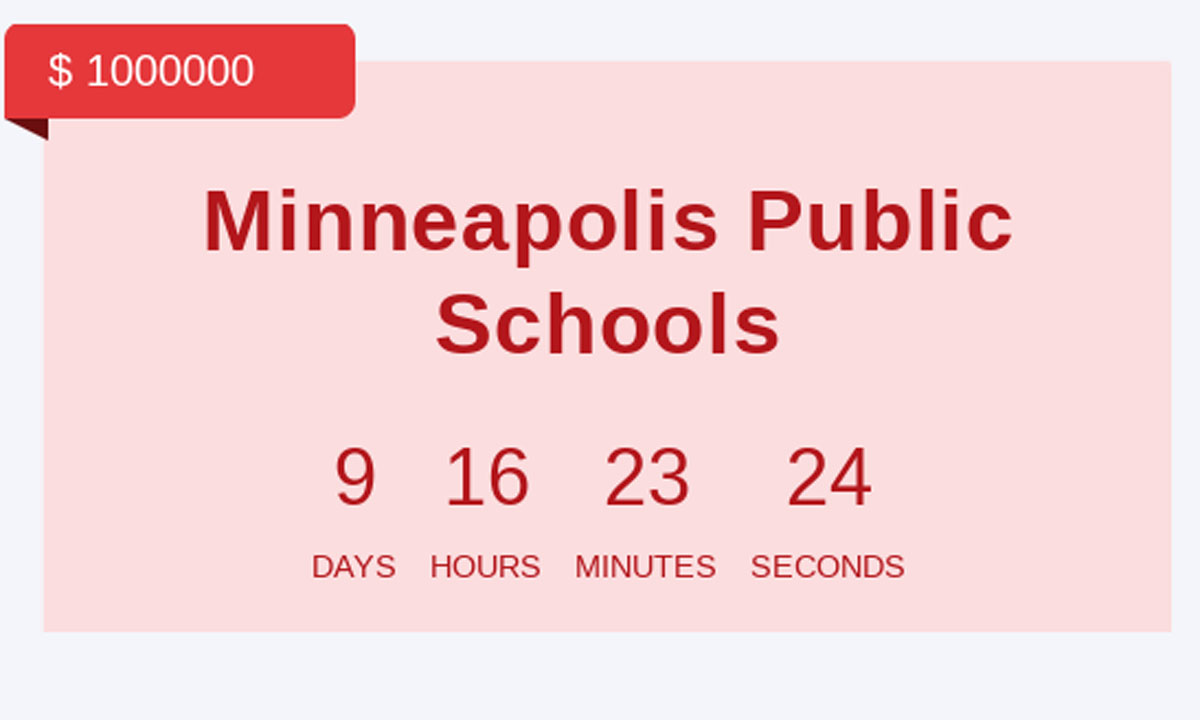
Minneapolis Public Schools appears to be the latest ransomware target in a $1 million extortion scheme that came to light Tuesday after a shady cyber gang posted to the internet a ream of classified documents it claims it stole from the district.
While districts nationwide have become victims in a rash of devastating ransomware attacks in the last several years, cybersecurity experts said the extortion tactics leveraged against the Minneapolis district are particularly aggressive and an escalation of those typically used against school systems to coerce payments.
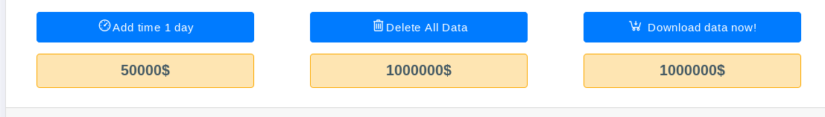
In a dark web blog post and an online video uploaded Tuesday, the ransomware gang Medusa claimed responsibility for conducting a February cyberattack — or what Minneapolis school leaders euphemistically called an “encryption event” — that led to widespread digital disruptions. The blog post gives the district until March 17 to hand over $1 million. If the district fails to pay up, criminal actors appear ready to post a trove of sensitive records about students and educators to their dark web leak site. The gang’s leak site gives the district the option to pay $50,000 to add a day to the ransom deadline and allows anyone to purchase the data for $1 million right now.
On the video-sharing platform Vimeo, the group, calling itself the Medusa Media Team, posted a 51-minute video that appeared to show a limited collection of the stolen records, making clear to district leaders the sensitive nature of the files within the gang’s possession.
“The video is more unusual and I don’t recall that having been done before,” said Brett Callow, a threat analyst with the cybersecurity company Emsisoft.
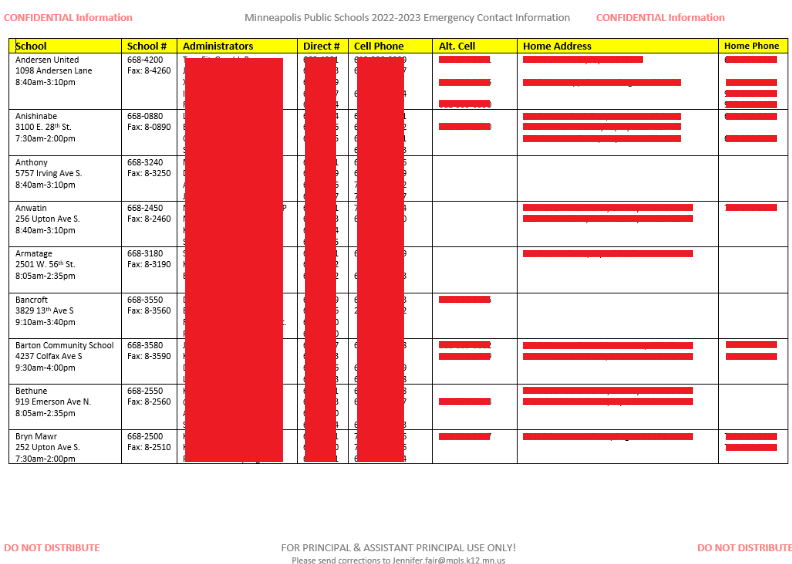
A preliminary review of the gang’s dark web leak site by The 74 suggest the compromised files include a significant volume of sensitive documents, including records related to student sexual violence allegations, district finances, student discipline, special education, civil rights investigations, student maltreatment and sex offender notifications.

The video is no longer available on Vimeo and a company spokesperson confirmed to The 74 that it was removed for violating its terms of service, which prohibits users from uploading content that “infringes any third party’s” privacy rights.
As targeted organizations decline to pay ransom demands in efforts to recover stolen files, Callow said the threat actors are employing new tactics “to improve conversion rates.”
“This is likely just an experiment, and if they find this works they will do it more frequently,” Callow said. “These groups operate like regular businesses, in that they A/B test and adopt the strategies that work and ditch the ones that don’t.”
Here’s a snippet of the video’s introduction (with all sensitive records omitted):
The Minneapolis school district hasn’t acknowledged being a ransomware victim, while Callow and other cybersecurity experts have been harshly critical of how it has disclosed the attack to the public. In a March 1 statement, the district attributed “technical difficulties” with its computer systems to the referenced “encryption event,” a characterization that experts blasted as creative public relations that left potential victims in the dark about the incident’s severity.
The district “has not paid a ransom” and an investigation into the incident “has not found any evidence that any data accessed has been used to commit fraud,” school officials said in the March 1 statement.
In a statement to The 74 Tuesday, the district said it “is aware that the threat actor who has claimed responsibility for our recent encryption event has posted online some of the data they accessed.”
“This action has been reported to law enforcement, and we are working with IT specialists to review the data in order to contact impacted individuals,” the statement continued.
Minnesota-based student privacy advocate Marika Pfefferkorn called on the district to be more forthcoming as it confronts the attack.
“First and foremost, they owe an apology to the community by not being explicit right away about what was happening,” said Pfefferkorn, executive director of the Midwest Center for School Transformation. “Because they haven’t communicated about it, they haven’t shared a plan about, ‘How will you address this? How will you respond?’ Not knowing how they are going to respond makes me really nervous.”
School cybersecurity expert Doug Levin, the national director of the K12 Security Information eXchange, said that district officials appear to have coined the term “encryption event,” but available information suggests the school system was the victim of “classic double extortion,” an exploitation technique that’s become popular among ransomware gangs in the last several years.
With its video and dark web blog, Medusa may have spent “a little more time and energy” than other ransomware groups in presenting the stolen data in a compelling package, “but the tactics seem to be the same,” Levin said. “Now that we have a group coming forward with compelling evidence that they have exfiltrated data from the system and it’s actively extorting them, that’s all I would need to know to classify this as ransomware.”
In double extortion ransomware attacks, threat actors gain access to a victim’s computer network, download compromising records and lock the files with an encryption key. Criminals then demand their victim pay a ransom to regain control of their files. Then, if a ransom is not paid, criminals sell the data or publish the records to a leak site.
Such a situation recently played out in the Los Angeles Unified School district, the nation’s second-largest school system. Last year, the ransomware gang Vice Society broke into the district’s computer network and made off with some 500 gigabytes of district files. When the district refused to pay an undisclosed ransom, Vice Society uploaded the records to its dark web leak site.
District officials have sought to downplay the attack’s effects on students. But an investigation by The 74 found thousands of students’ comprehensive and highly sensitive mental health records had been exposed. The district then acknowledged Feb. 22 that some 2,000 student psychological assessments — including those of 60 current students — had been leaked.
Districts that become ransomware targets could face significant liability issues. Earlier this month, the education technology company Aeries Software agreed to pay $1.75 million to settle a negligence lawsuit after a data breach exposed records from two California school districts. District families accused the software company of failing to implement reasonable cybersecurity safeguards.
Federal authorities have made progress in curtailing cybercriminals. In January, authorities seized control of a prolific ransomware gang’s leak site and earlier this month officials announced sanctions against seven men with ties to a Russian-based ransomware group that’s known to target schools.
At least 11 U.S. school districts have been the victims of ransomware attacks so far in 2023, according to Emsisoft research. Last year, ransomware victims included 45 school districts and 44 colleges.
In Minneapolis, a lack of transparency from the district could put affected students and staff at heightened risk of exploitation, Emsisoft’s Callow said.
“There absolutely are times when districts have to be cautious about the information they release because it is the source of an ongoing investigation,” he said. “But calling something a ransomware incident as opposed to an encryption event really isn’t problematic. Nor is telling people their personal information may have been compromised.”
Pfefferkorn, the Minneapolis student privacy advocate, said she’s concerned about the amount of data the school district collects about students and worries it lacks sufficient cybersecurity safeguards to keep the information secure. She pointed to Minneapolis schools’ since-terminated contract with the digital student surveillance company Gaggle, which monitors students online and alerts district officials to references about mental health challenges, sexuality, drug use, violence and bullying.
The district said it adopted the monitoring tool in a pandemic-era effort to keep kids safe online, but the unauthorized disclosure of Gaggle records maintained by the district could make them more vulnerable, she said.
There’s little recourse, she said, for students and educators whose sensitive records were already leaked by Medusa.
“It’s already out there and that cannot be repaired,” she said. “There’s information out there that’s going to impact them for the rest of their lives.”
Get stories like these delivered straight to your inbox. Sign up for The 74 Newsletter

;)
